It’s inconceivable to look at the information today with out listening to about hackers breaking into another corporate database and making off with delicate consumer login data and bank card particulars. It’d really feel to some people who the Web is changing into a relatively dangerous place to be, and it isn’t protected to do something on-line. However as with the offline world, it’s merely a matter of taking precautions and utilizing frequent sense. For those who do this, you’ll keep protected on-line and luxuriate in the advantages that the web has to supply.
Beneath, we have now outlined a mighty 33 tricks to keep protected on-line and reduce your danger of being hacked. Clearly, this isn’t going to assist if an organization you’re a buyer with will get hacked. However by following these easy, easy suggestions, you may reduce your publicity and include any injury.
Learn extra: What is a cybersecurity analyst?
QUICK ANSWER
Tricks to keep protected on-line embody utilizing encrypted accounts, minimizing your private data on-line, utilizing malware trackers, and utilizing stronger passwords. You also needs to watch out of clicking on e mail hyperlinks and downloading information with sure file codecs.
JUMP TO KEY SECTIONS
The assorted threats making it troublesome to remain protected on-line
Let’s begin with outlining among the threats at the moment doing the rounds on-line at present. On-line scams and risks come and go, and a few evolve into one thing else fully. However listed below are the frequent ones that stick round like a nasty scent and make it troublesome to remain protected on-line.
- Phishing (pronounced ‘fishing’) — that is whenever you’re despatched an e mail made to appear to be it got here from a trusted firm (your financial institution, insurance coverage firm, employer, and many others.). You’re then instructed there is a matter along with your account, and you might want to check in to ‘confirm your particulars.’ After all, they offer you a useful sign-in hyperlink that goes straight to their web site. How good of them.
- The Nigerian Prince e mail — we’ve ALL had this one (or variations of it.) You’re knowledgeable {that a} sure somebody died with out leaving a will, and there’s $50 million sitting unclaimed in a financial institution. The particular person gives to chop you into the cash in trade on your checking account particulars.
- The romantic stranger — feminine pals of mine on social media are hit notably arduous by this one. The scammer sweet-talks the particular person and ultimately tells them they love them. Then they make dedication guarantees and ask for cash.
- Ransomware — that is changing into an more and more frequent hazard on-line for firms. A hacker will lock down an organization’s total database and refuse to launch it except a ransom is paid. If the sufferer refuses, the database is remotely erased. Even when the sufferer pays, there’s no assure the database gained’t be erased anyway.
- Malware — the oldie however nonetheless alive and kicking. Planting viruses and malware on different folks’s computer systems will at all times be a straightforward technique to disrupt their lives.
- Id theft — once more, a quite common one. The extra data you allow on-line about your self, the extra you allow your self open to identification theft.
Figuring out your danger degree

Earlier than you progress on to the guidelines under, you must calculate what your precise danger degree is. That is known as menace modeling.
By this, I imply that every particular person has the next or decrease probability of being attacked. For instance, the President of the US has an especially high-risk degree due to who they’re and the conversations they’re having with folks every day. I, alternatively, a author with Android Authority, don’t have to fret in regards to the Chinese language authorities hacking into my cellphone conversations and listening to my pizza supply order.
In different phrases, in comparison with the US President, I’m a relatively boring man. I’ve a very totally different menace mannequin in comparison with a world politician or a celeb. You additionally must resolve the place on the size you fall based mostly on sure standards.
Do you fall into one of many following classes?

Listed here are some potential situations that would heighten your menace degree and make it troublesome to remain protected on-line.
- Do you could have a vengeful ex-partner (romantic or enterprise) who’s out to get grime on you?
- Do you could have a stalker?
- Are you going by way of a messy divorce or little one custody listening to?
- Are you a enterprise proprietor with delicate proprietary data that somebody is prone to steal from you?
- Are you a controversial, polarizing particular person?
- Are you a public official or movie star?
- Had been you a witness to a criminal offense and doubtlessly in peril?
Components like this could drive up your probability of being hacked on-line and make it much less seemingly you’ll keep protected when on the web. Nevertheless, on the flip aspect of the coin, 99% of persons are boring on a regular basis people who go to work, come dwelling, watch TV, and go to mattress. They’ve little or no to concern from a hacker who will deem them a waste of time.
However that’s to not say you must let your guard down fully. The purpose is to not panic and blow issues out of all proportion. Assess your doable weaknesses and tweak the next suggestions accordingly based mostly in your particular person wants.
33 tricks to reduce your hacking danger and keep protected on-line
Let’s now go into the assorted methods you may tighten up your on-line safety. Look upon this as a pleasant weekend venture.
Use encrypted e mail

As of late, everybody and their canine has a Gmail account. Everybody loves Gmail for its large quantity of cupboard space and cool features. Nevertheless, from a privateness perspective, it’s a nightmare.
True, they’ve two-factor authentication, so getting right into a 2FA-enabled Gmail account is extraordinarily troublesome. However any e mail and consumer metadata that hits US Google servers instantly fall beneath the jurisdiction of the US intelligence businesses, together with the Nationwide Safety Company. Within the UK, that might be MI5 and GCHQ. In truth, any nation signed as much as the Fourteen Eyes agreement routinely share data amongst themselves. Google complies with all requests at hand over no matter is demanded of them, so don’t count on them to place up any sort of a battle in your behalf.
As a substitute, use ProtonMail. That is an encrypted e mail service out of Switzerland, and the servers are in a closely guarded information middle inside a mountain, the situation of which is a giant secret. Switzerland’s extraordinarily strict information privateness legal guidelines all however be sure that any requests by governments and regulation enforcement at hand over emails and consumer metadata shall be politely rebuffed. Look upon it as the e-mail equal of placing all of your cash in a Swiss checking account.
You’ll be able to hook up a customized area, and it’ll even import all of your Gmail e mail, contacts, and calendar entries so that you can guarantee a easy transition over. You may get a free account, however for critical e mail energy customers, you might want to pay a small quantity yearly (which often consists of different Proton merchandise bundled in.)
For those who MUST use Gmail……

For those who actually can’t tear your self away from Gmail, then think about encrypting your emails to remain protected on-line. It’s not foolproof by any means, and a decided intruder with means will lastly crack it. However any informal opportunists will quickly quit.
One possibility which I just lately wrote about is FlowCrypt. It’s a Chrome extension that places an encryption button on the Gmail interface and converts your message into PGP (Fairly Good Privateness). The particular person on the different finish additionally wants FlowCrypt and may instantly decode the message.
After all, one other different is simply to obtain your e mail to an area e mail shopper comparable to Outlook or macOS Mail. Then set your on-line e mail service to delete the copies on their server.
Use a disposable e mail handle to join mailing lists
For those who resolve to join mailing lists, you actually shouldn’t be utilizing your major e mail handle. If anybody is monitoring you by way of your e mail, then they will see your tastes and proclivities based mostly on what e mail newsletters you subscribe to. So for mailing lists, you could have two choices – convert the e-newsletter to an RSS feed (I do know, old style) or use an nameless e mail handle (simply arrange one other Protonmail handle.)
You most likely suppose that RSS is all however useless. It’s true that its utilization is declining within the face of social media, nevertheless it’s nonetheless round. Join an RSS reader service, then join the e-mail e-newsletter with Kill The Newsletter. It should generate a randomly-generated e mail handle to join the record and an RSS feed to entry the newsletters once they come out.
Don’t click on on any hyperlinks inside emails
As we defined in a earlier part, individuals who ship phishing emails depend on you clicking a hyperlink within the e mail. This then sends you to a convincing-looking copy of an official web site, one which they management. When you enter your information into it, they’ve bought you.
That’s why the golden rule to remain protected on-line ought to at all times be – by no means, ever click on on any e mail hyperlinks. By no means. No exceptions. If you might want to verify the standing of a web based account, open your browser and manually sort within the web site handle. Then log in your self. In addition to, any professional firm would by no means ask you to click on an e mail hyperlink to ‘confirm your particulars’ for this exact purpose.
Be cautious of downloading e mail attachments
E-mail attachments are one other manner of passing on viruses and malware. Be extraordinarily cautious of what you obtain. One good Gmail characteristic is that they virus-scan something beneath 25MB in measurement. But when they will’t scan it, or the attachment seems to be suspicious in any manner, both contact the sender by way of one other communication methodology to ask about it or run the attachment by way of a virus scanner unopened, comparable to VirusTotal.
Change to encrypted messaging
We’re massive followers of WhatsApp right here at Android Authority, however like Gmail, WhatsApp is a privateness minefield. Regardless of boasting of end-to-end encryption, they’re sharing consumer metadata with their homeowners, Facebook. Sure, that Fb. The one that can promote your information off the again of a lorry for a greenback. That is regardless of an earlier promise to not share that metadata. And if WhatsApp just isn’t nice for that purpose, then it stands to purpose that Facebook Messenger is simply as unhealthy, if not worse.
Apple gadgets are good relating to encryption, however don’t suppose for a second that iMessage is a present from the encryption Gods. Sure, iMessage is encrypted end-to-end, however iMessage historical past is synced with iCloud, which sits on Apple’s servers that may – and does – get handed over to regulation enforcement authorities. That encryption out of the blue doesn’t look so good, does it?
The perfect different, by far, is Signal. No logs, no trackers, and no saved consumer data in any way, which implies nothing at hand over to the regulation if they arrive knocking on Sign’s door. The encryption protocols are additionally top-notch, and the app is totally free and open supply. You too can get a model on your pc and sync over the conversations.
Think about a extra privacy-based browser comparable to Firefox, Courageous, or Tor
Chrome is an effective browser, however being a Google-owned property, it’s as safe as Gmail. Forget Safari as nicely. As a substitute, think about a extra privacy-based different comparable to Firefox, Brave, and even Tor.
Tor has a popularity for being the browser everybody goes to entry the Darkish Internet. It is a barely unfair blemish, as Tor does loads of good as nicely to remain protected on-line. In international locations with oppressive regimes, Tor can actually imply the distinction between life and loss of life. Human rights activists, bloggers, journalists, opposition politicians….the record of people that profit from Tor each day is large.
The issue with Tor, although, is that it is rather gradual, because it has to undergo varied proxy relays to make sure your privateness. So don’t strive streaming any media by way of it. Plus, going anyplace close to the Darkish Internet wouldn’t be a good suggestion.
Whichever browser you find yourself selecting, be sure to update it as quickly as a brand new patch turns into out there.
Don’t go to a web site that doesn’t have a safety certificates

As of late, it’s normal Google coverage to deprioritize any web site and not using a safety certificates. A web site safety certificates is when it begins with HTTPS and has a padlock subsequent to the browser URL.
HTTPS ensures that there are not any “man within the center” assaults the place delicate consumer data has the potential to be intercepted. All big-name web sites at present use HTTPS, particularly e-commerce web sites and banking websites.
If a web site you’re visiting solely says HTTP, then it could be finest to present it a large berth. The location might not essentially be unhealthy by itself, however any data you place into that web site shall be insecure and broad open for the taking.
Maintain your cellular apps updated

It is a massive one which a stunning variety of folks don’t trouble with, in my expertise. They give the impression of being upon app updates as a ache within the neck and really inconvenient. However in actuality, it’s the alternative. They’re there to guard your cellphone by plugging safety vulnerabilities and bugs. So why shouldn’t you benefit from them?
Take away your cellular quantity from on-line accounts

Edgar Cervantes / Android Authority
In the case of a web based assault from a hacker, the primary level of weak spot is arguably a cell phone quantity. If you consider it, two-factor authentication codes can come as an SMS message. If a hacker is aware of your quantity, they will clone your SIM card and intercept these codes. Folks can impersonate you if they’ve a cloned cellphone along with your quantity. They might even have entry to your contacts with their data.
Due to this fact, strive to not give out your cellular quantity to too many individuals. In truth, make it a coverage to present it out extraordinarily sparingly. Take away it from as many on-line accounts as doable to remain protected on-line. If a web site or firm calls for a cellphone quantity, both give them a disposable pay as you go SIM card or, even higher, arrange a VoIP quantity with both Skype or Google Voice.
Don’t sideload unsigned and unverified cellular apps
Joe Hindy / Android Authority
This can be a controversial one, particularly with all you Android customers. In any case, sideloading is well-liked, even whether it is insecure. However there’s a purpose why Google has safety restrictions in place to discourage sideloading, and it isn’t to wreck your day.
For these unfamiliar with the terminology, sideloading is whenever you set up a cellular app by transferring the APK file immediately onto your gadget. It, subsequently, bypasses the Play Retailer and its safeguards, so if that app has malware in it, it isn’t going to be detected. Play it protected and stick with examined and verified apps on the Play Retailer. Any safety vulnerabilities may have been detected by Google and faraway from the Play Retailer (you’d hope, anyway.)
Use disposable digital debit playing cards
The outdated joke is that you would be able to purchase no matter you need if you happen to look on-line. If you’d like that mixed coathanger and cigarette lighter that performs German schlager music, then absolutely there’s a web site that caters to your wishes. However how are you aware if you happen to can belief that web site retailer along with your bank card particulars?
The reply is one-off disposable free digital debit playing cards. Transferwise, for instance, offers digital card numbers that you should use for one-off purchases. As soon as the transaction has gone by way of, you may cancel the quantity free of charge, stopping anybody from reusing it. Then you may generate a brand new quantity on your subsequent on-line buy. Rinse and repeat. You’ll be able to even put the cardboard on Apple Pay or Google Pay to make it simpler to pay on the on-line retailer. Ask your financial institution in the event that they, too, provide digital playing cards.
Construct up a web based persona
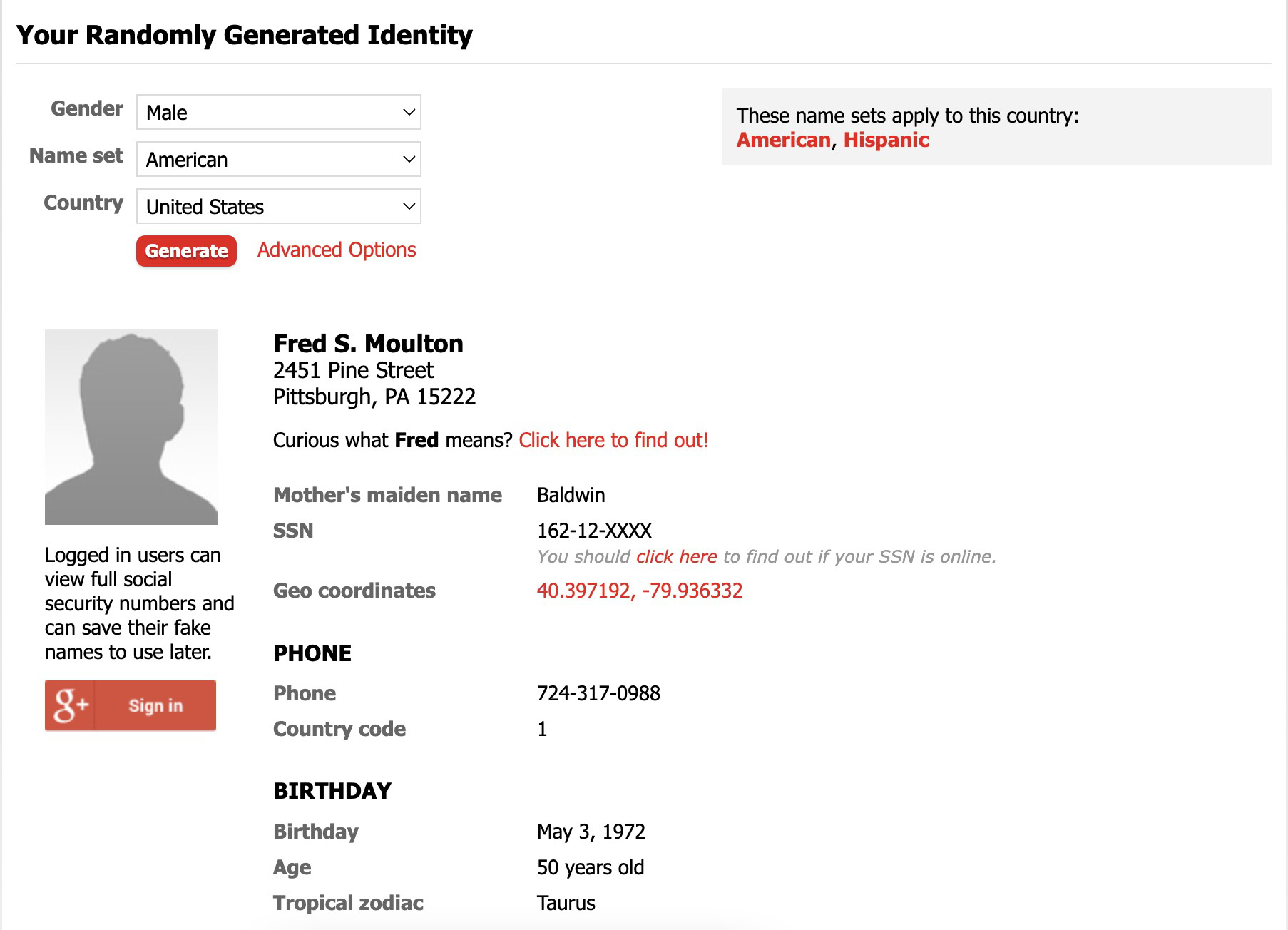
You’re going to suppose I’m going all James Bond right here with my fictional identification and backstory, however hear me out right here. What number of varieties have you ever crammed out which have requested on your identify, handle, cellphone quantity, date of delivery, zip code, and different pointless data? Info like that is what makes identification theft and information harvesting doable, so the very last thing you must do is put in your actual information if you wish to keep protected on-line.
For those who discover it a drag to maintain developing with faux data, a useful web site that randomly generates this data could make your life lots simpler. My go-to web site is Fake Name Generator. Enter your gender, nationality, and nation, and the positioning will spit out a brand new set of stats for you. Clearly, it goes with out saying that you just shouldn’t use faux data for authorized paperwork and to commit a criminal offense.
Obtain a password supervisor & enhance your passwords

Joe Hindy / Android Authority
Calvin just lately wrote a few nice articles on password managers and why you should use one. The most important weak level relating to on-line safety has at all times been the password. Two-factor authentication made the login password rather more safe, however that doesn’t imply you shouldn’t make an enormous effort along with your password. I wrote an article on this very subject not too way back, and you actually ought to learn it.
Making passwords like $40lkHß#Wq3VByL@ has its drawbacks, although – it’s inconceivable to recollect except you could have a photographic reminiscence. We use LastPass right here at Android Authority, however there are equally good alternate options, comparable to KeePass, 1Password, and Dashlane. In a pinch, you should use the password supervisor in your browser, however you shouldn’t if you happen to share your pc with different folks.
Use two-factor authentication
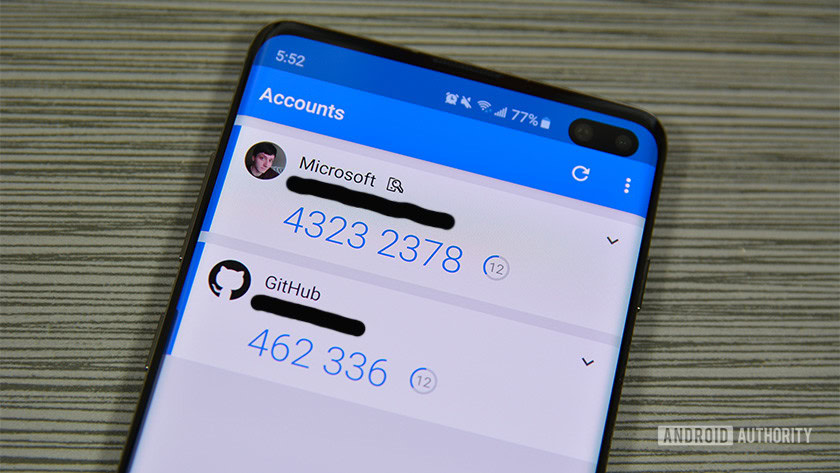
Together with a stonking massive password, you also needs to allow two-factor authentication on each platform that helps it. As of late, all the large gamers do – Google, Fb, Reddit, Twitter, Instagram, iCloud, Dropbox, and extra. If it’s there, use it. It may be a bit inconvenient to retrieve the additional code, however not as inconvenient as having your invaluable account hijacked.

For those who don’t need to use an authenticator app, you may get SMS messages along with your code, however that is insecure. The perfect methodology to remain protected on-line, outdoors an authenticator app, is a Yubico hardware key that slots right into a USB slot in your pc and makes use of your fingerprint to authenticate.
Use cloud storage platforms sparingly

Cloud storage platforms are very helpful, and I admit to having accounts on practically all of them. However they need to solely be used very sparingly, and delicate paperwork ought to keep off them altogether. Ought to delicate data actually be stored on another person’s server that you just don’t management? Higher to make use of a removable hard drive as an alternative or a NAS drive.
There’s nothing improper with utilizing cloud storage to maneuver information round between gadgets and to share information with different folks. However attempt to make it a behavior to not preserve information on there long-term. Cloud storage has the potential to be hacked, similar to another on-line firm.
Lock down your web site login web page

Edgar Cervantes / Android Authority
If in case you have your individual web site, and it runs WordPress, then you might want to make sure that it’s locked down tight. Up to now, I’ve had over 200,000 brute-force makes an attempt to get into my web site (over a seven-year interval), so I’m very conscious that having your individual web site is a really alluring goal for unhealthy actors on-line. This topic is an entire different article of its very personal, however listed below are the temporary highlights.
Use a VPN

For those who say “VPN” to somebody, they are going to most probably affiliate it with unlawful downloading or watching Netflix out of the country. However like Tor (which runs on VPNs), a VPN is an important privacy tool. Quick for Digital Personal Community, a VPN can redirect your web site visitors to a different server out of the country, thereby concealing your precise geographical location.
There are numerous VPN companies out there at present, all with various levels of high quality and price. However in my expertise, the most effective two are ProtonVPN (my present service and owned by Protonmail) and Tunnelbear. However try to avoid free VPN services – if you happen to’re not paying for the product, you’re the product.
Rigorously think about what sensible dwelling gadgets you must have

Edgar Cervantes / Android Authority
However Internet of Things (IoT) gadgets can have very lax privateness insurance policies and unhealthy safety features, and this could let unhealthy folks into your non-public life. One instance is safety cameras linked by way of the web. All it takes is for somebody to hack by way of the firewall, and out of the blue they will see inside your own home. Child displays could be one other dangerous factor to have.
I’m not saying to be fully paranoid about all these things. They are often extraordinarily helpful devices and make life extraordinarily handy and comfy. Simply present common sense and take into consideration the doable downsides of introducing all this stuff into your own home. Be selective in what you put in and train good safety practices.
Set up a malware detection instrument and firewall
I’ve heard it typically stated today that malware detection instruments and firewalls are not wanted. That the web “has moved on.” But these are the identical individuals who find yourself with hacked Fb accounts and click on on e mail hyperlinks. The unhappy reality is that malware has gone nowhere and intends to go nowhere. It has at all times been round. So it could be extremely irresponsible to not have some safety.
Granted, Home windows does have a built-in firewall and a malware instrument known as Microsoft Defender. Nevertheless it isn’t the most effective on the market, and there are undoubtedly better alternatives for Windows PCs. On the Apple aspect, malware is much less frequent (don’t assault me, Apple haters), however you may nonetheless get all of the big-name firms providing Mac variations of their merchandise. It’s higher to be protected than sorry. There are additionally malware detection instruments for iPhone and Android.
Set up all safety patches for Home windows and Mac computer systems
Palash Volvoikar / Android Authority
For those who use a Home windows PC or a Mac (extra a Home windows PC than a Mac), you might get actually irritated on the fixed calls for to replace your PC with the newest patches. However you must keep in mind that the extra your pc will get patched, the safer it will likely be.
Password-protect your own home Wi-Fi community
Ankit Banerjee / Android Authority
Having an open Wi-Fi community (one which isn’t password-protected) is a very unhealthy thought. Not solely will you could have neighbors and strangers leeching off your connection, however anybody can use your web to obtain something unlawful. Whether or not that’s music, motion pictures, or, God forbid, pornography, that shall be on you if the police come knocking on the door. Failure so as to add a password to your Wi-Fi community just isn’t a viable protection in court docket.

If there isn’t a password on your router, go to the router web page instantly and add one. Regular password guidelines apply. No pet names, squirrel noises, tribal oaths, or birthdays.
Make backups of every thing in your pc and cellphone

That is one other factor that we continuously preach right here at Android Authority Loss of life Star HQ. Again up every thing. Make a backup of the backup of the backup. Automate that backup. Encrypt that automated backup. Be obsessive about backups.
Make your cellphone passcode longer and extra advanced
Telephone passcodes are often 4 digits by default. Whereas this makes remembering them and typing them in very handy, it doesn’t take lengthy for somebody to brute-force their manner in. Nevertheless, if you happen to prolong that PIN code to 6 digits, it out of the blue turns into rather more troublesome and longer to interrupt in. Lengthen it even additional to 9 digits, and in need of a supercomputer, no one has an opportunity of stepping into your gadget.
On an iPhone, you may change your passcode by:
- Go to Settings > Face ID & Passcode.
- Faucet Change Passcode.
- When you enter your outdated passcode, faucet Passcode Choices.
- Select both Customized Numeric Code (all numbers) or Customized Alphanumeric Code (letters and numbers.)
On an Android cellphone, you may change the passcode by:
- Go to Settings > Safety > Display screen Lock (the wording might range relying in your Android mannequin.)
- Enter your outdated PIN.
- Select the fashion of the brand new PIN and enter it.
Encrypt your pc
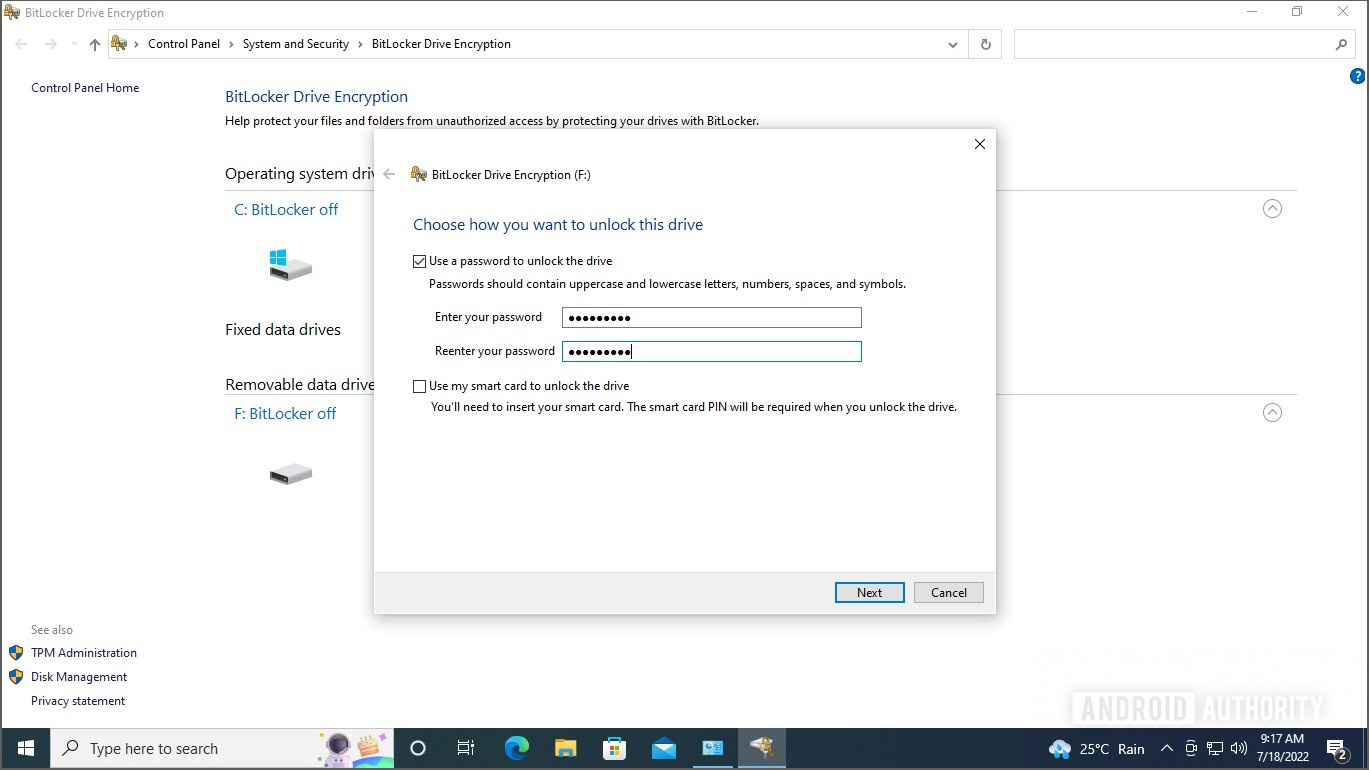
Encrypting your pc has change into a lot simpler over the previous years. Home windows provides Bitlocker to anybody with knowledgeable model of Home windows, and Mac computer systems have built-in encryption with FileVault.
Watch out with sure file sorts
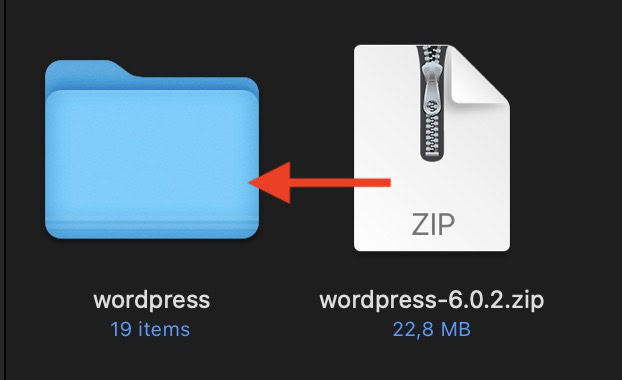
Be further cautious with information which have the format EXE, ZIP, RAR, ISO, or something which is an working system script. If unsure, don’t open them.
However saying that, different file codecs are usually not immune. It’s doable, for instance, to cover a virus or a hidden script inside a JPG picture file.
Run any downloaded suspicious information by way of VirusTotal
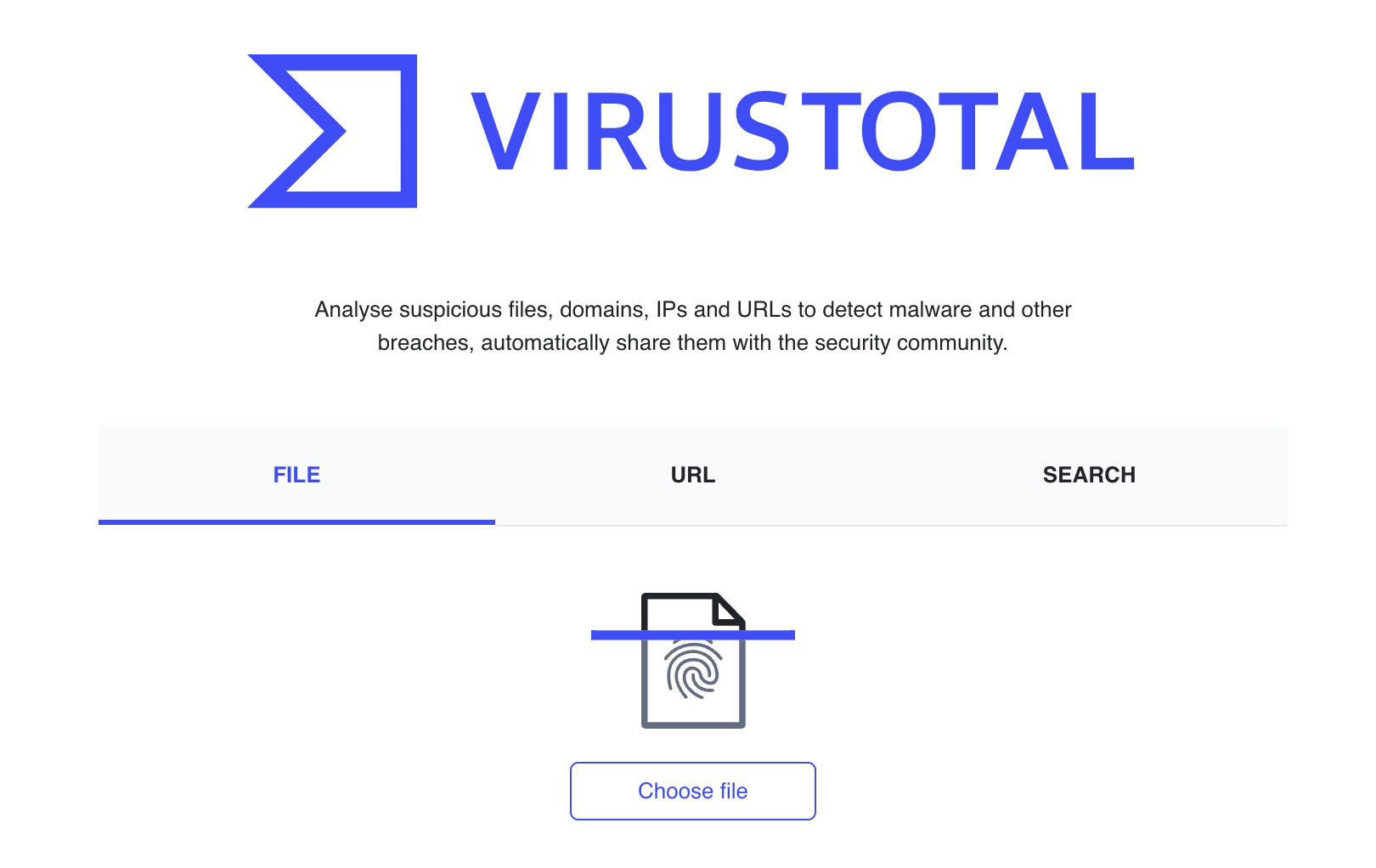
For those who completely must obtain a file, run it by way of VirusTotal first. This scans information on-line with out having to obtain them first, utilizing a number of anti-virus companies. It additionally checks URLs. You’ll be able to add already downloaded information, scan undownloaded ones by offering the URL, or e mail a suspicious file.
The method is made even easier by means of browser extensions, so you may simply right-click on the file hyperlink.
Give an identification password to firms you’re a buyer with

Inform your cable firm, cellphone firm, and web supplier to not speak to anybody about your account with out offering a password first. Social engineering is changing into extra frequent, which is when somebody calls up pretending to be you to realize particulars about your account.
So put a password or PIN in your account to cease this from occurring. Most massive firms have already got this characteristic, however some require you to choose in by requesting it.
Watch out what you publish on social media

Joe Hindy / Android Authority
Social media is the place all of the cool children hang around, and naturally, firms depend on earning profits with Facebook, Instagram, TikTok, and others. So there are particular benefits to utilizing social media. It’s additionally enjoyable to attach with your pals. However after all, we come again once more to revealing an excessive amount of of ourselves, which might result in identification theft.
Once more, all of it comes right down to frequent sense and judgment, however the primary highlights could be:
- Don’t enable anybody to tag you in images.
- Maintain all private stuff to Associates Solely.
- Maintain your cellphone quantity off social media and deny all requests to add your contacts.
- Don’t verify in at varied places.
- Don’t publish images of your little one or different youngsters.
Use faux solutions for safety questions
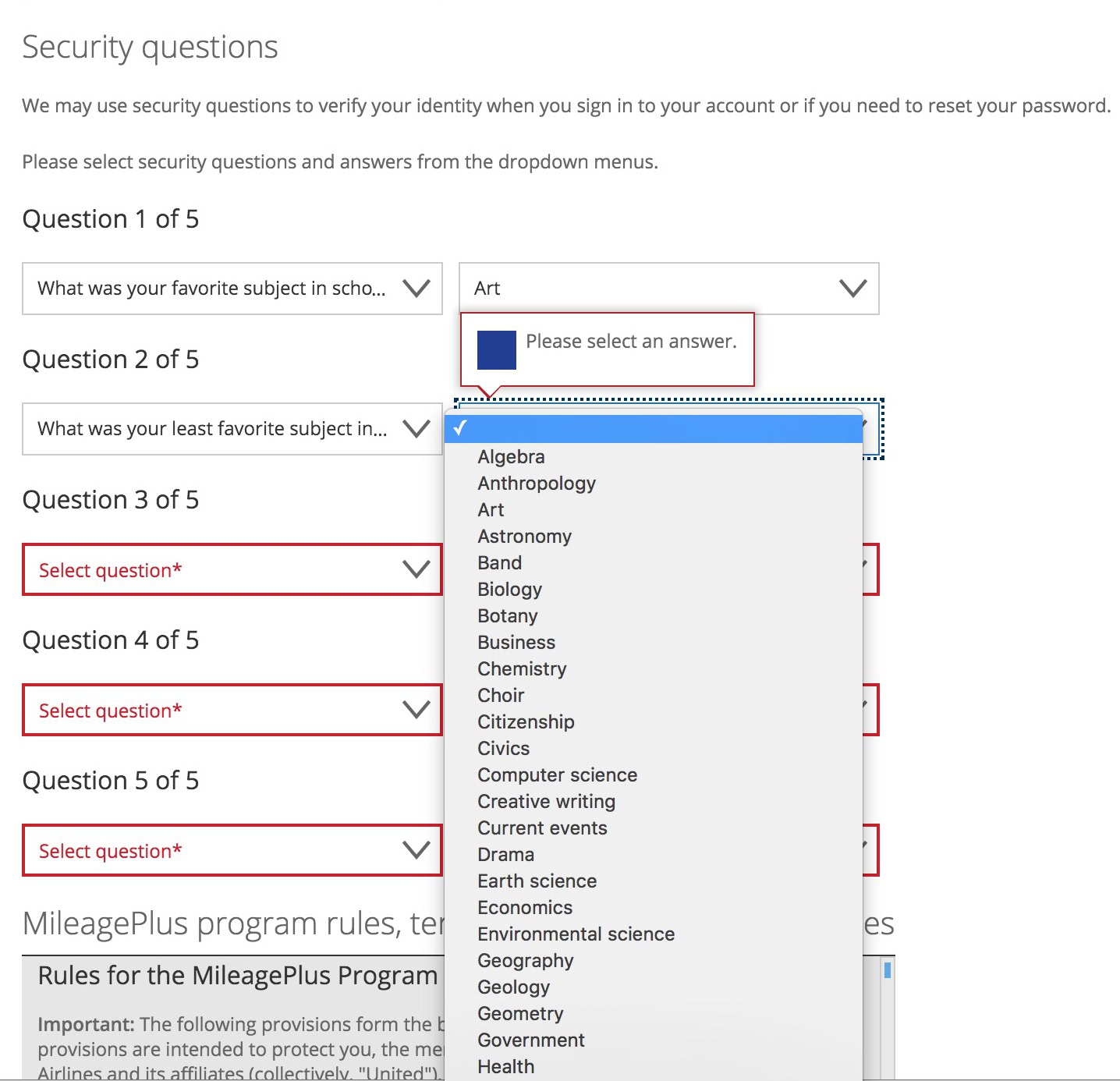
I coated this in my article on making a strong password. When making replies to safety questions, many individuals inform the reality. So anybody with data of that particular person is probably going going to know the reply. So as an alternative, make up foolish replies that no one will ever guess.
- The place have been you born? In a hospital.
- The place did you first stay? In a home on a road.
- Who was your first trainer? Some outdated woman with unhealthy breath.
- The place did you go in your first date? Paradise.
- What was your first automotive? One with 4 wheels and doorways.
- What was your first job? Incomes cash.
- What time of the day have been you born? I wasn’t a clock. I used to be a bit busy.
- What’s your grandmother’s first identify? Granny.
Cowl your pc webcam

Kris Carlon / Android Authority
You’d be hard-pressed to seek out a pc today and not using a built-in webcam. They’re so small and unobtrusive that they are often straightforward to miss. But when anybody can achieve entry to that webcam, they will actually look proper at you. They’ll document you, hearken to you, see your environment, and extra. Sci-fi paranoia? Not quite.
The best answer is to place a chunk of tape over the webcam. However you may as well purchase proper webcam covers which you’ll slide backwards and forwards. Extremely really useful.
Don’t click on on brief hyperlinks
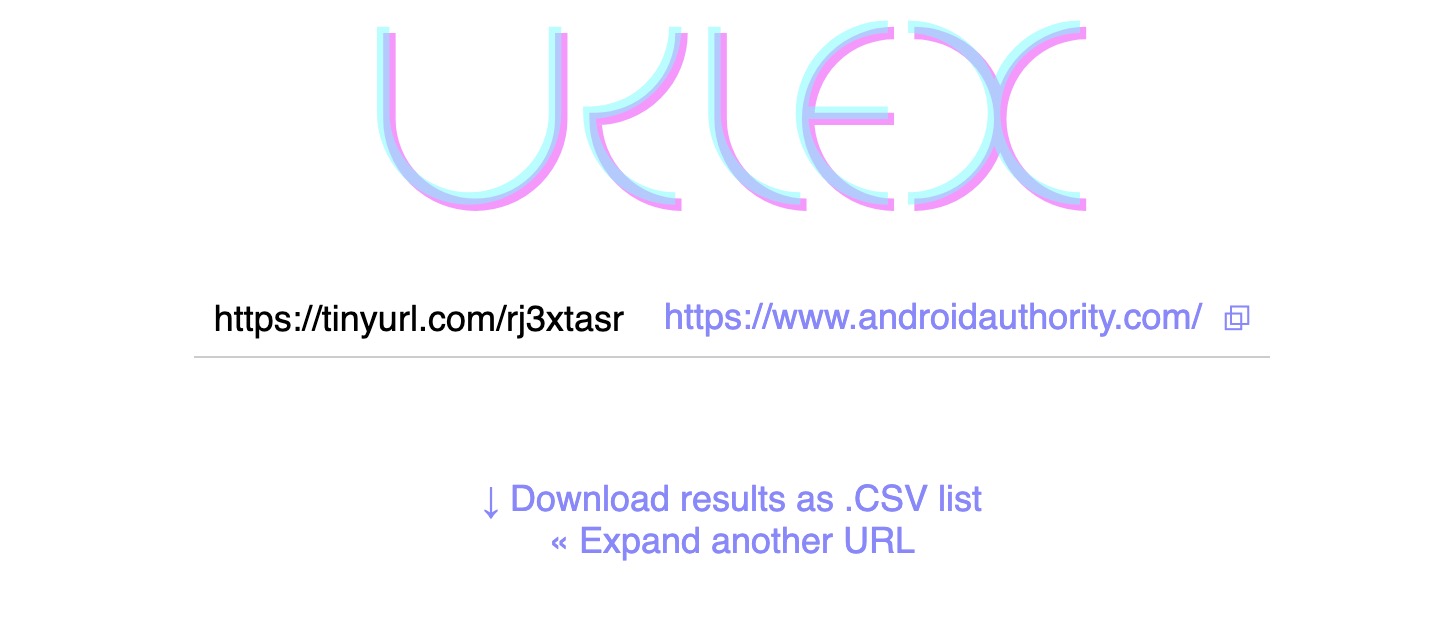
Quick hyperlinks are designed to make hyperlinks extra enticing to click on. Firms additionally use them as a advertising and marketing instrument. The New York Instances, for instance, makes use of the nyti.ms area for brief hyperlinks. However the issue with brief hyperlinks is that, for the overwhelming majority of them, you don’t have any thought the place they are going to result in. A New York Instances hyperlink can clearly be trusted, however what a few tinyurl.com hyperlink? A Bitly hyperlink? These can lead anyplace, comparable to an contaminated web site or malware-infected file.
Attempt to keep away from brief hyperlinks altogether, however if you happen to should click on one, run it by way of Text Expander first. It should reveal the hyperlink’s vacation spot, and you may then resolve if it seems to be legit or not.
Shut down all inactive and unneeded on-line accounts
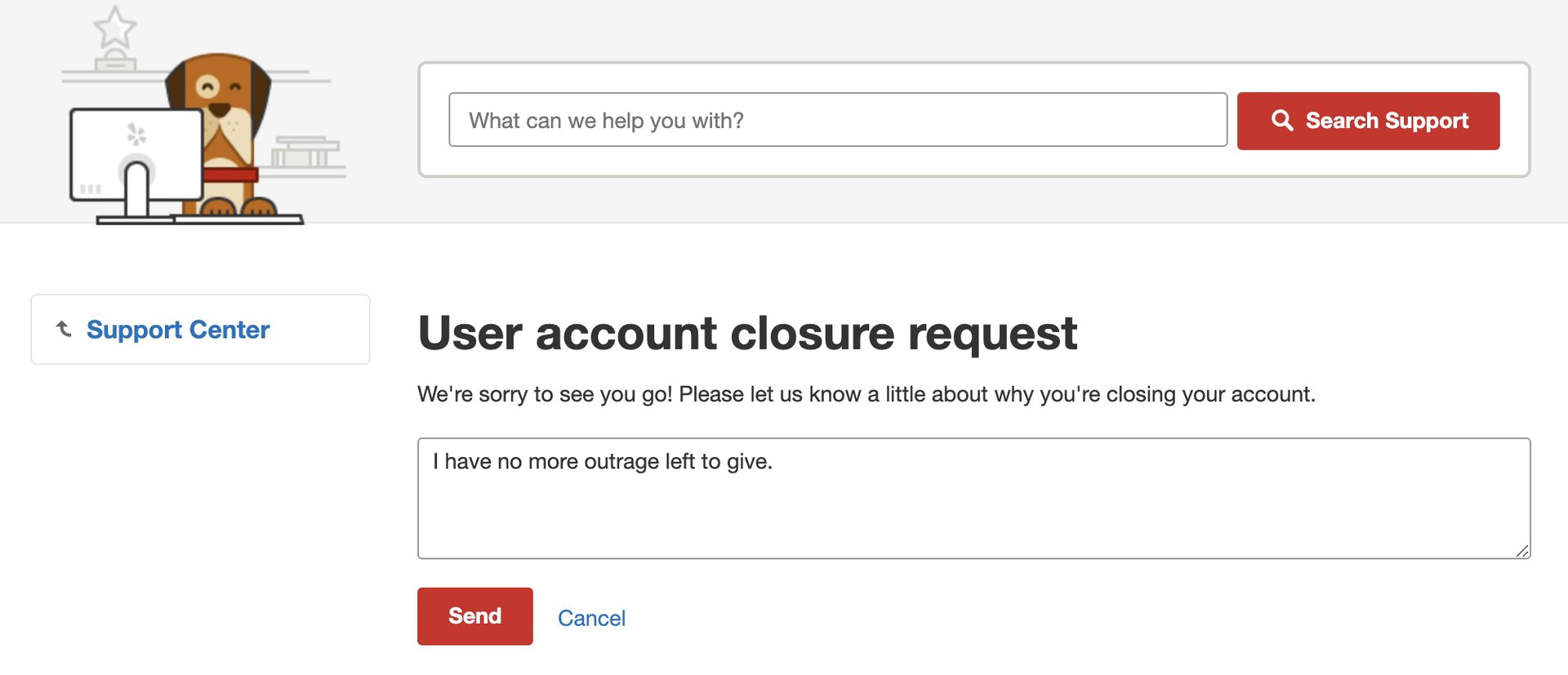
I’m positive you all have ten Gmail accounts, varied Twitter accounts, and possibly a few Reddit accounts. However do you actually want all of them? If any of these accounts are caught in a knowledge breach, your private data is uncovered. So if you happen to don’t want an account anymore, delete it.
Simply go to the account settings and search for the account deletion possibility. Some accounts shall be made inactive for 30 days in case you alter your thoughts, however others are shut down instantly. The less accounts you could have floating round on the market, the higher.
Log off from gadgets and accounts whenever you’re not utilizing them
Adam Birney / Android Authority
For those who use a pc that’s shared by others (household, pals, colleagues, acquaintances), then the chance is there for them to snoop in your account. So when you’re completed checking your e mail or social media, sign off.
FAQs
The frequent consensus is that it isn’t price it anymore. Even the inventor of PGP has given up on it, saying it has change into too sophisticated for the typical consumer to make use of.
Metadata is any figuring out information on a file. Picture metadata could be the identify of the digital camera that took the photograph. E-mail metadata may very well be when the e-mail was despatched.
It’s an encrypted connection between your pc and the server upon which the web site you’re visiting sits on. A safe connection stops data from being intercepted whereas in transit between you and the web site (and vice-versa).
A VPN redirects your web exercise to a server both in your nation or one other nation. This makes it inconceivable for anybody to listen in on what you’re doing or to hint you again to your precise location.
No firm goes to confess to it, and if they’re, it could definitely take loads of pc processing energy to pay attention 24/7. Though Fb is suspected of it, the consensus is that they are not.
Source link
[Denial of responsibility! reporterbyte.com is an automatic aggregator of the all world’s media. In each content, the hyperlink to the primary source is specified. All trademarks belong to their rightful owners, all materials to their authors. If you are the owner of the content and do not want us to publish your materials, please contact us by email – reporterbyte.com The content will be deleted within 24 hours.]










